Serious rootkit concerns
What really happens when you turn on your computer? How does it go from a power switch to your desktop? Although many detailed explanations exist, the basics are:
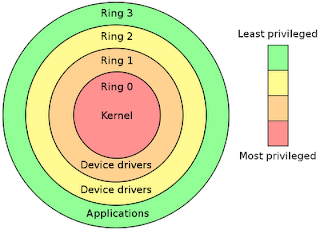
Rings range from -N...0...+N (with -N having the most privileges and +N having the least privileges). Using the boot sequence list above, the rings roughly translate to:
As you can imagine, the bad guys want to "own" or control the computer as deeply and early as possible in the boot sequence. Although there are a host of malicious malware out there (viruses, worms, trojans, spyware, keyloggers, etc), the tool of choice for most hackers is a rootkit/bootkit. Rootkits are designed to be very stealthy, difficult to remove, and very powerful. The following table provides a brief overview of the evolution of rootkits and the concerning trend towards bare-metal control and infection that persists after wiping the hard drive:
As you can see, the emphasis is starting to shift away from traditional Ring 3 malware towards Ring 0 bootkits and Ring -3 hardware rootkits. With the increase in hardware standards, protocols, and ROM space, a hacker's job is made that much easier (especially considering many hardware manufacturers still aren't taking the threat seriously).
Personally, I think it's only a matter of time until we see a 64-bit, worm-propagated, cross-platform, bootloader-aware, encryption-savvy bootkit that resides in persistent, antivirus-unreachable Ring -3 space....oh wait, that's pretty much the Stoned bootkit's ToDo list.
Okay, enough of the FUD, how do we protect ourselves? To be absolutely safe, do the following:
1. Care about security.
Okay, assuming burying your computer isn't an option:
1. Be paranoid about security.
3. Use a NAT hardware firewall and software firewall.
4. Use a non-IE web browser (less targeted). If Firefox is your browser of choice, there are a lot of security add-ons available - play around to find the best matches for you.
5. Use a non-Windows operating system (less targeted).
6. Disable floppy and CD-ROM booting and password-protect your BIOS.
7. If multi-booting on the same machine, avoid bootloaders and instead install each operating system on its own drive (with its own MBR) and switch between them using the BIOS boot device selector.
8. Buy a motherboard with BIOS protection (e.g. Intel Trusted Execution Technology or Phoenix TrustedCore).
9. Only browse known, safe sites (not exactly secure due to XSS, DNS cache poisoning, SSL vulnerabilities, PKI vulnerabilities, and hacked routers / web servers...but it's a start)
Have any other ideas? Let me know!
Update (Feb 2010): The new rootkit nasty on the block is Tdss rootkit...scary stuff!
- Power switch
- Chipset (Northbridge/MCH/IMC, Southbridge/ICH/PCH, ...)
- CPU
- System BIOS
- CMOS (BIOS settings)
- Power-On Self Test (POST)
- Video card BIOS
- Other device BIOS (RAID, SCSI, NIC, IDE/ATA, PCI, ...)
- RAM (system memory)
- Firmware & Plug and Play (USB, Firewire, ...)
- If signaled, System Management Mode (SMM)
- If present, Type-1 Hypervisor (virtualization)
- Master Boot Record (MBR) of bootable drive, including bootloaders (GRUB, LILO, NTLDR, Boot Camp, ...)
- Operating System kernel
- Device drivers
- Applications (executable programs)

Rings range from -N...0...+N (with -N having the most privileges and +N having the least privileges). Using the boot sequence list above, the rings roughly translate to:
| Ring -3 | Chipset, System BIOS, CMOS, Device BIOS, RAM (system memory), Firmware, and Plug and Play |
| Ring -2 | System Management Mode (SMM) |
| Ring -1 | Type-1 Hypervisor (virtualization) |
| Ring 0 | Operating System kernel |
| Ring 1 & 2 | Device drivers |
| Ring 3 | Applications |
As you can imagine, the bad guys want to "own" or control the computer as deeply and early as possible in the boot sequence. Although there are a host of malicious malware out there (viruses, worms, trojans, spyware, keyloggers, etc), the tool of choice for most hackers is a rootkit/bootkit. Rootkits are designed to be very stealthy, difficult to remove, and very powerful. The following table provides a brief overview of the evolution of rootkits and the concerning trend towards bare-metal control and infection that persists after wiping the hard drive:
| Ring -3 | Tribble, CoPilot, and Firewire-subversion (2003-2006), ACPI BIOS rootkit (2006), PCI rootkit (2006), memory-subversion (2007), European card swipe malware (2008), Core BIOS rootkit (2009), AMT rootkit (2009) |
| Ring -2 | SMBR (2008) |
| Ring -1 | SubVirt (2006), Blue Pill (2006) |
| Ring 0 | Cuckoo's Egg (late 1980's - first Unix rootkit), lrk3 (1996 - first Linux rootkit), NT Rootkit (1999 - first Windows rootkit), Sony XCP rootkit (2005), Mebroot bootkit (2007), Stoned bootkit (2009) |
| Ring 3 | Hacker Defender (2003) |
As you can see, the emphasis is starting to shift away from traditional Ring 3 malware towards Ring 0 bootkits and Ring -3 hardware rootkits. With the increase in hardware standards, protocols, and ROM space, a hacker's job is made that much easier (especially considering many hardware manufacturers still aren't taking the threat seriously).
Personally, I think it's only a matter of time until we see a 64-bit, worm-propagated, cross-platform, bootloader-aware, encryption-savvy bootkit that resides in persistent, antivirus-unreachable Ring -3 space....oh wait, that's pretty much the Stoned bootkit's ToDo list.
Okay, enough of the FUD, how do we protect ourselves? To be absolutely safe, do the following:
1. Care about security.
"Most people, I think, don't even know what a Rootkit is, so why should they care about it?"2. Bury your computer.
- Thomas Hesse (President, Sony BMG Global Digital Business)
"The only secure computer is one that's unplugged, locked in a safe, and buried 20 feet under the ground in a secret location ...and I'm not even too sure about that one."
- Dennis Hughes (FBI official)
Okay, assuming burying your computer isn't an option:
1. Be paranoid about security.
"Only the paranoid survive."2. Install, and regularly update, antivirus and antispyware protection.
- Andrew Grove (Time Magazine's Man of the Year, 1997)
3. Use a NAT hardware firewall and software firewall.
4. Use a non-IE web browser (less targeted). If Firefox is your browser of choice, there are a lot of security add-ons available - play around to find the best matches for you.
5. Use a non-Windows operating system (less targeted).
6. Disable floppy and CD-ROM booting and password-protect your BIOS.
7. If multi-booting on the same machine, avoid bootloaders and instead install each operating system on its own drive (with its own MBR) and switch between them using the BIOS boot device selector.
8. Buy a motherboard with BIOS protection (e.g. Intel Trusted Execution Technology or Phoenix TrustedCore).
9. Only browse known, safe sites (not exactly secure due to XSS, DNS cache poisoning, SSL vulnerabilities, PKI vulnerabilities, and hacked routers / web servers...but it's a start)
Have any other ideas? Let me know!
Update (Feb 2010): The new rootkit nasty on the block is Tdss rootkit...scary stuff!


Comments
Post a Comment
Keep it clean and professional...