Secure RHEL6 with OpenSCAP
If you're a brand new Linux server administrator and you don't have a strong handle on the plethora of security risks and remediation steps, OpenSCAP is a nice starter tool.
I couldn't find a nice guide for Fedora / CentOS / Red Hat Enterprise Linux 6 so I put one together:
(note: I recommend trying this on a backup or test machine first)
1. Install the scanner engine:
7. Repeat step 5 above and review any remaining errors or failures you may want to fix manually.
_________________
Resources:
P.S. If you want to take your security to the next level, you might want to check out Linux Malware Detect, ModSecurity, and Suricata/OSSIM
(note: I recommend trying this on a backup or test machine first)
sudo yum -y install openscap openscap-utils
scap-security-guide
2. At the time of this writing, there wasn't an automatic fix for the "Control-Alt-Delete" behavior so apply fix manually:
sudo sed -i 's/exec \/sbin\/shutdown -r now "Control-Alt-Delete pressed"/exec \/usr\/bin\/logger -p security.info "Control-Alt-Delete pressed"/' /etc/init/control-alt-delete.conf
sudo sed -i 's/select idref="disable_ctrlaltdel_reboot" selected="true"/select idref="disable_ctrlaltdel_reboot" selected="false"/g' /usr/share/xml/scap/ssg/content/ssg-rhel6-xccdf.xml3. Unless you're running a server for the government, you don't need their login banner so disable that rule:
sudo sed -i 's/select idref="set_system_login_banner" selected="true"/select idref="set_system_login_banner" selected="false"/g' /usr/share/xml/scap/ssg/content/ssg-rhel6-xccdf.xml
4. Scan your server for potential issues (this is a simulated run only, no changes will be made to your server)
sudo oscap xccdf eval --profile stig-rhel6-server-upstream --results /tmp/oscap-results.xml --report /tmp/oscap-results.html --cpe /usr/share/xml/scap/ssg/content/ssg-rhel6-cpe-dictionary.xml /usr/share/xml/scap/ssg/content/ssg-rhel6-xccdf.xml
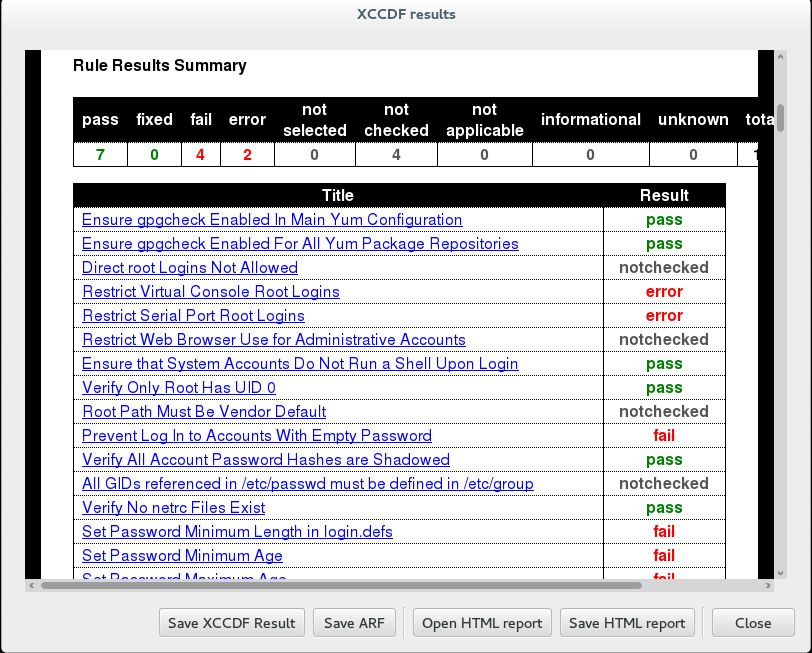
5. If you have a browser installed on the server, you can open /tmp/oscap-results.html. Otherwise, copy /tmp/oscap-results.html to another machine, open in browser, and search for Remediation script sections for any fail or error entries. If any of those fixes are not desired, repeat step 4 above replacing set_system_login_banner with the desired Rule ID.
6. Once you have disabled any rules that you don't want applied, you're ready to fix your system! Run the scan again using the --remediate flag to automatically apply fixes provided for your server profile (note: not every issue has an automatic fix):
sudo oscap xccdf eval --remediate --profile stig-rhel6-server-upstream --results /tmp/oscap-results.xml --report /tmp/oscap-results.html --cpe /usr/share/xml/scap/ssg/content/ssg-rhel6-cpe-dictionary.xml /usr/share/xml/scap/ssg/content/ssg-rhel6-xccdf.xml
7. Repeat step 5 above and review any remaining errors or failures you may want to fix manually.
_________________
Resources:
- https://fedorahosted.org/scap-security-guide/
- http://people.redhat.com/swells/scap-security-guide/RHEL/6/output/rhel6-guide.html
- http://pkgs.org/centos-6/epel-testing-i386/scap-security-guide-0.1.17-1.20140524git2eeeca7.el6.noarch.rpm.html
P.S. If you want to take your security to the next level, you might want to check out Linux Malware Detect, ModSecurity, and Suricata/OSSIM


It looks as if this will not work on CentOS since the xccdf format uses CPE validation and if you use the rhel6 xccdf file it will show the tests as not applicable. I have not found a workaround as of yet besides just running the oval definitions. Are you aware of how to suppress the CPE validation?
ReplyDeleteCheck out SCAP Workbench at https://fedorahosted.org/scap-workbench
ReplyDeleteIt's a lot more convenient for rule selection and value changes than sed.
Regarding CentOS, support has recently been added, see https://github.com/OpenSCAP/scap-security-guide/pull/567
Thanks, Martin, for the update and tip!
ReplyDelete